In a previous blog post, I was going to capture using two Access Points with 802.11r disabled. It was disabled but, 802.11v was baked into the firmware. This slowed me down(not in the roaming sense, how I was doing my setup). But I needed to continue with this test to see how fast things moved. So if you look back at this post, it talks about what devices and how I created the SSID to look. I did disable 802.11r, but I’m still going to use 802.1X(capital X). Why not just WPA2, well, because I’m using RADIUS. And, the end goal is to see about using a Cloud RADIUS.
So, I have my test setup, and I’m walking from one Access Point to the other. I nice handy tool I use to see if I have roamed visually is called Network Analyzer. It quickly shows my current BSSID and also has an IP block Scanner. So somewhat handy.
During my little walk, I had my MacBook capturing the channel I had set both Access Points on. And, used Airtool for the packet capture.
Now that I have my frames captured, in the wireless world, packets are called frames. I can narrow down what to look for as my capture was over 14,000 frames(yeah, I have lots of other things on these APs, 10 Chromecast devices are very, very chatty).
But what do I look for? Since we’re moving between Access Points, you need to look for what is called Association and Reassociation requests.
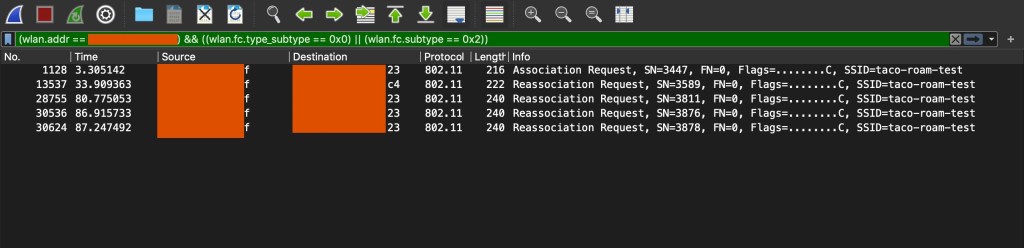
You loaded your pcap into Wireshark, now time to filter down for what you’re looking for.
And, thanks to François Vergès for having this handy “Wireshark Most Common 802.11 Filters” PDF, searching is now 100% easier in Wireshark.
wlan.fc.type_subtype == 0x0
wlan.fc.type_subtype == 0x2
From the handy chart, we need those two options, if you combine those, you should have something that looks like this:
(wlan.fc.type_subtype == 0x0) || (wlan.fc.type_subtype == 0x2)
I see the frames we’re looking for, but now I need to find the MAC of my client.
i.e. wlan.addr == CC:46:D6:00:00:00
And then we combine all that Wireshark magic and then we’re shown a few lines from the pcap.
(little disclaimer – that first pcap image didn’t have everything I needed so I made another pcap and filtered for what we need.)
So here’s what we have now, with just 802.11v enabled on this “taco-roam-test” SSID. You can see my client device connect to the first Access Point ending in 23, then me walking to the next AP ending in c4, then back to 23.
So about 3.3 seconds in, I join the SSID, then checked to make sure I have an IP address, then switch over to the Network Analyzer app, then start walking towards AP c4. Now once I saw in the Analyzer app that my device changed BSS units, I walked closer to that AP a few more seconds then started walking back towards AP 23. I was trying to walk the same path again. Also, my office is roughly 10,000 Sq ft. I probably walked about halfway between the APs before it switched, which would mean about ~40 feet away from AP 23. Also, both radios are set for 19 dBm(no external antennas).
So, what did we learn, well nothing yet, other than a roam from and back to an Access Point. Well, yeah, we learned about some tools and how to filter with Wireshark. Now I need to enable 802.11r and do it all over again.
Also, here’s a little handy Column you should add to Wireshark, Time Delta. Right-click on a Column section, select Column Preferences. Hit the “+” to add a Column, give it a Title, I called my Time Delta. The type will be Custom, then enter the following in Fields:
frame.time_delta_displayed
Now you have a Column that shows the Time Delta.